With the rise of digitalisation, all industries and sectors have gone digital by adopting emerging trends and switching to cloud platforms. This change and evolution in the infrastructure has been essential in streamlining operations and providing a better storage solution.
Can you imagine working with piles and piles of papers stacked up everywhere in the office while handling customer queries?
This is quite a messy situation and with the digitalisation of storing and processing documents and information, banking has achieved a level of efficiency and productivity like never before.
While there are many benefits to the digitalisation wave, one cannot forget about the network vulnerabilities or security loopholes that endanger the entire banking system.

One small mistake and the entire database, which includes customer banking details, personal details, asset information and more are leveraged in the hands of hackers. Besides the loss of reputation and hefty fines, there is a risk of this data being sold in the black market, jeopardising the information of many customers and investors.
It is impossible to ignore the rising trend of digitalisation; however, it is always wise to stay aware of all the mishaps that could lead to critical information falling into the wrong hands.
What Leads to Security Vulnerabilities in the Banking Sector?
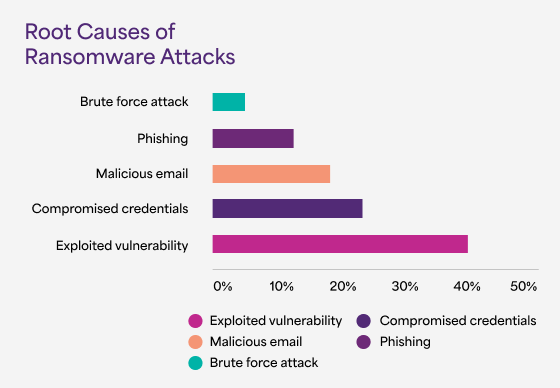
![Sandy_Tech-22_Single-11 [Converted]-01 1](https://celerityx.com/wp-content/uploads/2024/07/Sandy_Tech-22_Single-11-Converted-01-1.png)
Loopholes in the network or security system lead to cybercrimes. According to Check Point Research, cyberattacks around the globe increased by more than 38% in 2022 compared to 2021. Besides, the same research indicates that the maturity of AI technology will lead to additional cybercrimes in 2023.
What leads to cyberattacks? Let’s start from the beginning. A computer network comprises various devices connected to facilitate the exchange of information and the sharing of documents. The computer devices communicate with one another through communication protocols or digital interconnections.
A hacker exploits the weakest link in this connection, and once a particular device is exploited, the entire network is endangered.
Loopholes that Lead to Security Vulnerabilities
Let’s understand the loopholes that lead to network vulnerabilities.
Technology Vulnerabilities
One of the most common reasons for loopholes that lead to network vulnerabilities is technology vulnerabilities. Legacy systems are not designed keeping the modern security threats in mind and are challenging to update according to the present security needs. Besides, the complex IT infrastructure adds further complexities to maintaining security across all components (mobile banking apps, ATMs, and online platforms).
New Technological Platforms
Cloud computing and artificial intelligence have emerged as potential solutions to streamline many operations in the banking sector. However, they also present significant security threats.
For instance, the data stored in cloud platforms is stored somewhere in a physical server of a third-party provider in an off-site location. A malicious actor with authorization to data storage, either within the company or cloud provider’s side, may manipulate or leak confidential data. Data breaches at the cloud provider’s end can also jeopardise the integrity and security of data.
Moreover, AI is giving rise to more intricate cyber attacks, like zero-day attacks. Zero-day attacks target vulnerabilities or security flaws that weren’t detected before the attack happened.
One of the recent incidents of zero-day attacks is related to Barracuda. Barracuda Networks, an MNC providing cybersecurity services related to email and web networks, announced a zero-day vulnerability (CVE-2023-2868) in its Barracuda Email Security Gateway (ESG).
Hackers are utilising AI algorithms to analyse huge amounts of data and identify potential flaws in software that have yet to be discovered by the developers themselves.
Human Errors
When an employee falls prey to phishing emails, hackers can easily exploit and access any system in a network. These emails trick the employees into clicking on malicious links or revealing secret information that can grant access to the entire network infrastructure.
These are called social attacks where a hacker uses social engineering tactics, which is often an email that allures the recipient to give in important information. The hacker can then utilise that information, for instance, company credentials, to log in and access the protected data.
Another report, World Economic Forum Global Cybersecurity Outlook 2022, mentions that a staggering 95% of data breaches have been caused by human errors. Whether it is through stolen credentials, phishing emails, or simply due to an error, people play a major role in data breach incidents.
Inadequate Security Measures
The importance of strong passwords with multiple and different types of characters cannot be understated. Systems with weak passwords are easily exploited. According to Keeper Security’s Workplace Password Malpractice Report, around 44% of employees use the same credentials for both their personal and work-related accounts. Besides, inefficiencies in addressing patch vulnerabilities in operating systems, networks, firmware, and applications also leave the entire infrastructure hanging by a thread and expose the system to known attacks.


Security Breaches in the Banking Sector:Stories of Huge Losses Due to Minute Errors
The journey to a big milestone begins with a single step. We can say the same about data breaches and cyber-attacks. Let’s understand this by reading the case of the First American Financial Corp Data Breach. The breach was reported in May 2019, and around 885 million financial and personal records related to real estate transactions were exposed due to a common website design error. The error is called a Business Logic Flaw, and any authentication protocol doesn’t protect the webpage link that directs to sensitive information to verify user access.
However, this exposure was not initiated by any hacker; a data leak caused it. A data leak is when sensitive data is unintentionally exposed physically, on the Internet, or through any form. The hacker can access the sensitive data without much effort.
Consequences of Data Breaches
However, this exposure was not initiated by any hacker; a data leak caused it. A data leak is when sensitive data is unintentionally exposed physically, on the Internet, or through any form. The hacker can access the sensitive data without much effort.
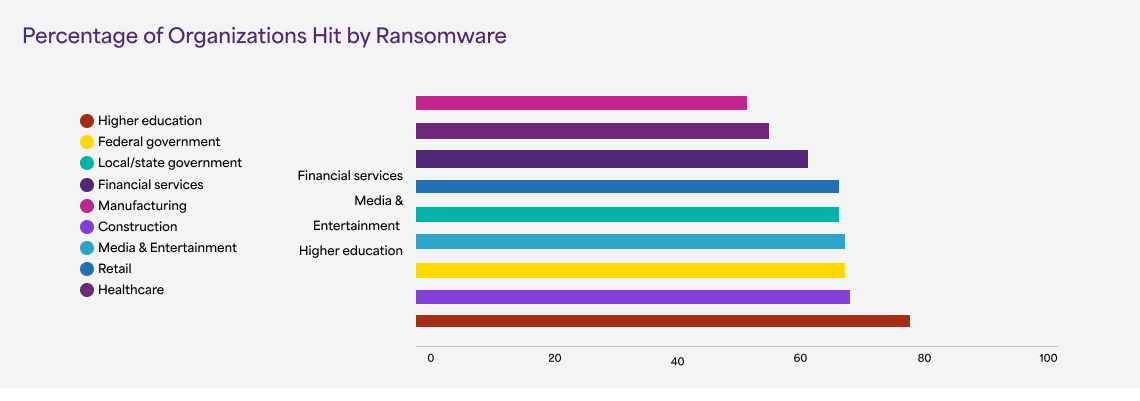
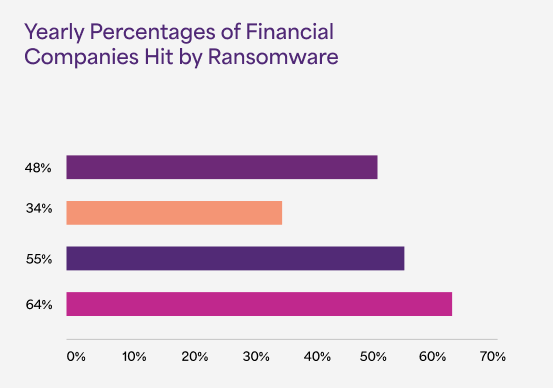
Importance of Taking the Right Steps at the Right Time
While the methods of committing cyber crimes have advanced; however, the advanced security techniques and protocols are robust enough to keep the hackers out of the system. Here are some of the steps that you can take to boost your network security:
1. Update the software as quickly as possible because the operating systems and applications may contain zero-day vulnerabilities. The only way to safeguard against this attack is to patch the software whenever the update is available.
2. Ensure that the network is entirely visible to the security teams so that they can track every user behaviour. It is best to map every device connected to the network, including IoT devices, smartphones, and remote work laptops.
3. Invest in perimeter protections, like firewalls, VPN (virtual private network) encryption, multi-factor authentication, 2-factor authentication, and more.
4. Use cloud-adapted network security tools, like SDP (Software Defined Perimeter), to create encrypted bubbles around every user.
5. Identify and detect DDoS attacks with packet monitoring software tools. These tools can track DNS Requests, DNS Responses, User Datagram Protocols, and others. A sudden spike in packet variants will alert security teams.
6. You can invest in OneX to make your network more secure and unbelievably fast. It is an all-in-one solution guaranteeing 100% uptime for core banking features and includes built-in Unified Threat Management features, like stateful firewall, endpoint security, and IDS/IPS.
The Bottom Line,
Every network is vulnerable to security attacks; however, problems can be easily avoided with the implementation of the timely assessment of the network security posture to detect and prevent vulnerable attacks and keep network away from cyber security risks.

Protect your network from cyber threats and outdated technology. Strengthen your operations with OneX, your go to security solution.









